GSM Threats
There’s no doubt that mobile devices make our lives easier. But the more upgraded and advanced a device becomes, the more threats it bears.
Please, note, that the below presented list of threats is far from being complete. You can find a detailed threat description in Mobile Security Reference Architecture by Federal CIO Council and United States Department of the Interior (May, 2013).
Key Threat Sources:
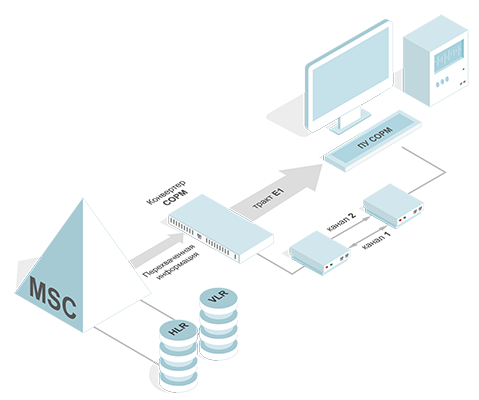
1. SORM — System for Operative Investigative Activities
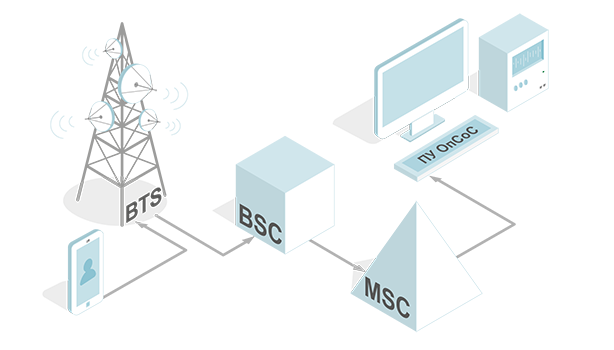
2. Service Providers (Mobile Operators)
3. Mobile Devices and Control System Producers (Operating System)
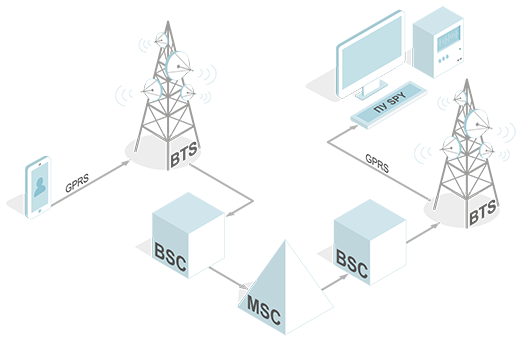
4. Communication Interception (Interceptions complexes: active, semi-active, passive, other ways of interception)
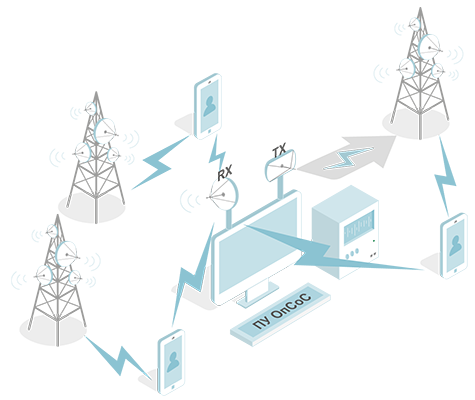
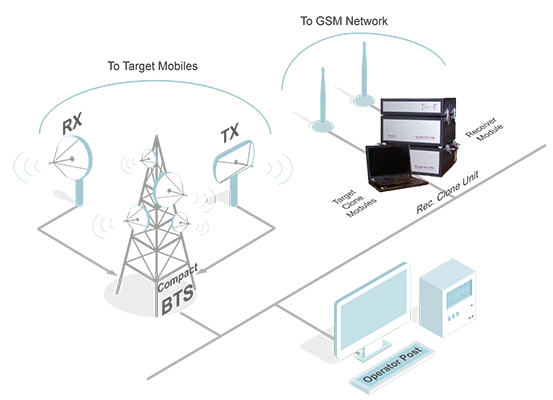
How to Protect:
1. to Use dynamic identifiers (IMSI+Ki, IMEI)
2. to Keep the algorithm A5/1.2.3.0 under control
3. to Secure SIM Policy
4. To Change Voice
5. To substitute calling number
6. No Location Data
7. No Billing Statistics
8. No Call proves between the subscribers
9. to block hacker attacks on HLR level
10. To intercept and block any SMS, including Silent SMS (Stealth SMS) on SMSC level
Working Principles:
To gain control over a handset or a SIM card, one needs to know its identifiers. Network are kept under government control and all of them are connected to the proper facilities that are used to perform surveillance activities.
The principal identifier for any mobile device is IMEI, i.e. International Mobile Equipment Identity. IMEI is transmitted to the network.
There is also a subscriber identifier – IMSI, International Mobile Subscriber Identity, in other words, it is used to identify the user in a cellular network. The parameter is transmitted to the network.
MSISDN, Mobile Subscriber Integrated Services Digital Number, is a subscriber public number used for service integration within GSM, UMTS and other standards. MSISDN is not transmitted to a network, but is interconnected with IMSI.
Having these identifiers at hand makes it possible to collect the following information:
— Using IMEI – it is possible to get access to all the IMSIs that are loaded on the SIM, thus it is an easy access to the billing data as well as location updates, SMS, MMS, calls, URLs, log ins, passwords etc.,
— Having IMSI one can get access to a handset’s IMEI and a SIM cards’s IMSI, that were used in these handsets, therefore the billing data also becomes available.
Secure SIM does not belong to any network operator, there is no public access to MSISDN as well as to the billing System.
How a SIM registers in a network and chooses a cell
1. When you turn on a mobile device with a Reular SIM, the handset scans the frequencies and chooses a cell with the strongest signal. When a Secure SIM connects to a cellular network that has the second strongest signal. This algorithm provides a set of security measures that prevent the information from interceptions.
2. Once the device is synchronized and identified, a regular SIM registers in an network according to Algorithm A3. This protocol calculates the SRES key, that allows to complete the authentication procedure. To calculate the SRES key in Algorithm A3, the Protocol uses IMSI and Ki identifiers. A regular SIM card has a fixed ‘IMSI’ is fixed that cannot be changed, when a Secure SIM has several profiles at a time with their own IMSI + Ki set.
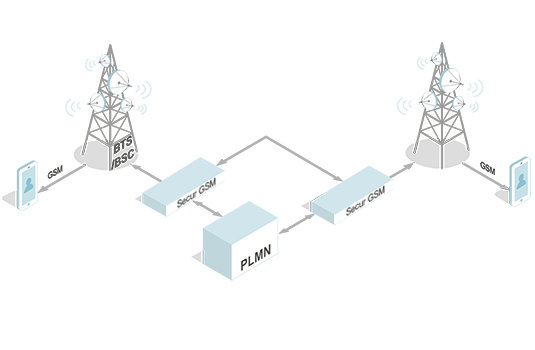
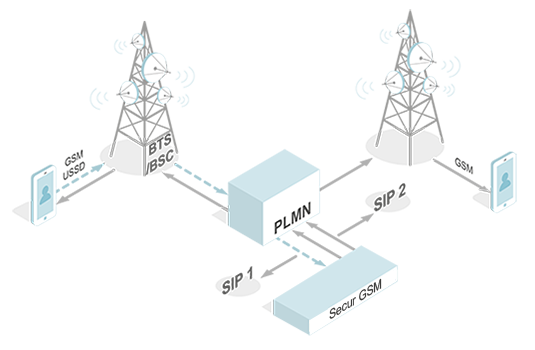
GSM ciphering
It is the operator that determines the ciphering level. Unlike a regular SIM, the Secure SIM has a special applet that tracks the ciphering level and notifies the user in case it is going down.
Calls
To make a call using a regular SIM, a subscriber dials a number. The phone sends an ALERT signal to the BSS (Base Station Subsystem) via the high-speed FACCH control channel, and then to MSC (Mobile Switch Centre). MSC sends a message ‘AddressComplete’ to the caller. And the two subscribers are getting connected.
If MSISDN of either of the subscribers is known, it is possible to get all the calling session data or to intercept the call with an intercept complex.
ДОБАВИТЬ СТРОЧКУ:Secure SIM call scheme is different. First, there are two ways of calling, these are a Call Through (Camel) call and Call Back call. Call Through (Camel) call - Secure SIM user dials a number, a SIM card applet catches the call, and redirects it to the service number. The calling number is transmitted onto our automatic telephone system (PBX) via the ciphered signal channel. Therefore, all Outbound calls from a Secure GSM SIM card are performed onto our service number of our network. PBX forwards the call to the end user.
Call Back call - User dials a number and at this point the call seems to drop. But in fact, at this very time the SIM sends the encrypted command to the server PBX via the signal channel. HBX via SS7 requests a VLR a permission to allocate a temporary number, Mobile Station Roaming Number (MSRN). Once an operator have allocated the MSRN to the Secure SIM, the SIM cards calls the MSRN. The Secure SIM user picks up, the AB leg starts. After that PBS Secure GSM starts calling the second subscriber. When the second subscriber picks up, the AG legs opens.
These ways it is impossible to get any operator billing information, as there is no data and facts what operator Secure SIM is connected to. The SIM has no public MSISDN, therefore no access to IMSI, Ki and IMEI. Even if the subscriber is being eavesdropped, it is not possible to find out who the subscriber was calling to and talking to. A call session consists of 2 legs (AB leg and AG leg), between the two legs there is a Secure GSM PBX.
Incoming Call (Regular SIM)
Once an Outbound Call has been made (Subscriber A calls Subscriber B), the calling session gets a TMSI (Temporary Mobile Subscriber Identity) within a VLR coverage, a traffic provider terminates the call, the calling session has been established, the Subscriber B gets a call. If either of the Subscribers is using a regular SIM, the Network Operator receives and records locations of the Subscribers, call duration, handset model (Subscriber A) etc.
Incoming Call (Secure SIM)
Once an Outbound Call has been made (Subscriber A), a Secure SIM gets a virtual DID number. It receives a call from a network, transforms it into a SIP protocol and routes it to Secure GSM PBX. Secure GSM defines the subscriber with the allocated DID and starts the call. There is no evident connection between the two Subscribers, as the connection is not direct and goes via Secure GSM PBX, that gives no possibilities to detect the Subscribers locations.
Phonetic (Voice) Print
Network Operators are actively using phonetic control systems to detect subscribers using their Voice Prints. Unlike a regular SIM Secure SIM provides an opportunity to change acoustic characteristics for Inbound and Outbound calls. The feature is extremely helpful especially if it is an Outbound call to a regular SIM.
HLR requests
Network Operators have a set of standard requests, that guarantee Roaming Services for guest Subscribers. Unfortunately it’s a titbit not only for the Subscribers but also hackers attacking SS7 networks. The attacks look like regular requests to HLR operator via SS7. The requests are aimed at getting an up-to-date data about the subscriber (IMSI, Ki, IMEI etc.). HLR is being an integral part of our infrastructure; we intercept any attacks and notify our subscribers about them. The feature is included to PING.
Stels SMS
Silent SMS
To manage a handset or its preinstalled applications, hackers use Type 0 Messages or so-called ‘Silent SMS’ or ‘Stealth SMS’. The key points of these type of SMS are not shown or kept on a handset. The Silent SMS request goes as well via HLR. Having HLR on our we intercept any attacks and notify our subscribers about them. The feature is included to PING.
Secure SIM has no billing at Network Operator’s side that makes it impossible to get, record and analyze any information about subscribers (CDRs, Location, Voice print etc).
Our System manages and controls all the process occurring on the three levels: Subsbcriber’s Handset (a handset with a changed system), our own identification module (Secure SIM with the imbedded applets) as well as the network level (we fully control HLR, MSC and SMSC).
PS
It is important to remember that a regular handset is highly insecure. Operators are constantly improving their tools to collect and analyze information about Subscribers using billing patterns. Having access to all national Network Operators Billing Systems, it is possible to find out a lot about a Subscriber.
Please, note, that the below presented list of threats is far from being complete. You can find a detailed threat description in Mobile Security Reference Architecture by Federal CIO Council and United States Department of the Interior (May, 2013).
Key Threat Sources:
1. SORM — System for Operative Investigative Activities

Image 1. SORM
2. Service Providers (Mobile Operators)

Image 2. Service Providers
3. Mobile Devices and Control System Producers (Operating System)

Image 3. Operating System
4. Communication Interception (Interceptions complexes: active, semi-active, passive, other ways of interception)

Image 4. Communication Interception

Image 5.Fields of Application
How to Protect:
1. to Use dynamic identifiers (IMSI+Ki, IMEI)
2. to Keep the algorithm A5/1.2.3.0 under control
3. to Secure SIM Policy
4. To Change Voice
5. To substitute calling number
6. No Location Data
7. No Billing Statistics
8. No Call proves between the subscribers
9. to block hacker attacks on HLR level
10. To intercept and block any SMS, including Silent SMS (Stealth SMS) on SMSC level
Working Principles:
To gain control over a handset or a SIM card, one needs to know its identifiers. Network are kept under government control and all of them are connected to the proper facilities that are used to perform surveillance activities.
The principal identifier for any mobile device is IMEI, i.e. International Mobile Equipment Identity. IMEI is transmitted to the network.
There is also a subscriber identifier – IMSI, International Mobile Subscriber Identity, in other words, it is used to identify the user in a cellular network. The parameter is transmitted to the network.
MSISDN, Mobile Subscriber Integrated Services Digital Number, is a subscriber public number used for service integration within GSM, UMTS and other standards. MSISDN is not transmitted to a network, but is interconnected with IMSI.
Having these identifiers at hand makes it possible to collect the following information:
— Using IMEI – it is possible to get access to all the IMSIs that are loaded on the SIM, thus it is an easy access to the billing data as well as location updates, SMS, MMS, calls, URLs, log ins, passwords etc.,
— Having IMSI one can get access to a handset’s IMEI and a SIM cards’s IMSI, that were used in these handsets, therefore the billing data also becomes available.
Secure SIM does not belong to any network operator, there is no public access to MSISDN as well as to the billing System.
Difference between a Regular and a Secure SIM
How a SIM registers in a network and chooses a cell
1. When you turn on a mobile device with a Reular SIM, the handset scans the frequencies and chooses a cell with the strongest signal. When a Secure SIM connects to a cellular network that has the second strongest signal. This algorithm provides a set of security measures that prevent the information from interceptions.
2. Once the device is synchronized and identified, a regular SIM registers in an network according to Algorithm A3. This protocol calculates the SRES key, that allows to complete the authentication procedure. To calculate the SRES key in Algorithm A3, the Protocol uses IMSI and Ki identifiers. A regular SIM card has a fixed ‘IMSI’ is fixed that cannot be changed, when a Secure SIM has several profiles at a time with their own IMSI + Ki set.

Image 6. Secure SIM

Image 7
GSM ciphering
It is the operator that determines the ciphering level. Unlike a regular SIM, the Secure SIM has a special applet that tracks the ciphering level and notifies the user in case it is going down.
Calls
To make a call using a regular SIM, a subscriber dials a number. The phone sends an ALERT signal to the BSS (Base Station Subsystem) via the high-speed FACCH control channel, and then to MSC (Mobile Switch Centre). MSC sends a message ‘AddressComplete’ to the caller. And the two subscribers are getting connected.
If MSISDN of either of the subscribers is known, it is possible to get all the calling session data or to intercept the call with an intercept complex.
ДОБАВИТЬ СТРОЧКУ:Secure SIM call scheme is different. First, there are two ways of calling, these are a Call Through (Camel) call and Call Back call. Call Through (Camel) call - Secure SIM user dials a number, a SIM card applet catches the call, and redirects it to the service number. The calling number is transmitted onto our automatic telephone system (PBX) via the ciphered signal channel. Therefore, all Outbound calls from a Secure GSM SIM card are performed onto our service number of our network. PBX forwards the call to the end user.
Call Back call - User dials a number and at this point the call seems to drop. But in fact, at this very time the SIM sends the encrypted command to the server PBX via the signal channel. HBX via SS7 requests a VLR a permission to allocate a temporary number, Mobile Station Roaming Number (MSRN). Once an operator have allocated the MSRN to the Secure SIM, the SIM cards calls the MSRN. The Secure SIM user picks up, the AB leg starts. After that PBS Secure GSM starts calling the second subscriber. When the second subscriber picks up, the AG legs opens.
These ways it is impossible to get any operator billing information, as there is no data and facts what operator Secure SIM is connected to. The SIM has no public MSISDN, therefore no access to IMSI, Ki and IMEI. Even if the subscriber is being eavesdropped, it is not possible to find out who the subscriber was calling to and talking to. A call session consists of 2 legs (AB leg and AG leg), between the two legs there is a Secure GSM PBX.
Incoming Call (Regular SIM)
Once an Outbound Call has been made (Subscriber A calls Subscriber B), the calling session gets a TMSI (Temporary Mobile Subscriber Identity) within a VLR coverage, a traffic provider terminates the call, the calling session has been established, the Subscriber B gets a call. If either of the Subscribers is using a regular SIM, the Network Operator receives and records locations of the Subscribers, call duration, handset model (Subscriber A) etc.
Incoming Call (Secure SIM)
Once an Outbound Call has been made (Subscriber A), a Secure SIM gets a virtual DID number. It receives a call from a network, transforms it into a SIP protocol and routes it to Secure GSM PBX. Secure GSM defines the subscriber with the allocated DID and starts the call. There is no evident connection between the two Subscribers, as the connection is not direct and goes via Secure GSM PBX, that gives no possibilities to detect the Subscribers locations.
Phonetic (Voice) Print
Network Operators are actively using phonetic control systems to detect subscribers using their Voice Prints. Unlike a regular SIM Secure SIM provides an opportunity to change acoustic characteristics for Inbound and Outbound calls. The feature is extremely helpful especially if it is an Outbound call to a regular SIM.
HLR requests
Network Operators have a set of standard requests, that guarantee Roaming Services for guest Subscribers. Unfortunately it’s a titbit not only for the Subscribers but also hackers attacking SS7 networks. The attacks look like regular requests to HLR operator via SS7. The requests are aimed at getting an up-to-date data about the subscriber (IMSI, Ki, IMEI etc.). HLR is being an integral part of our infrastructure; we intercept any attacks and notify our subscribers about them. The feature is included to PING.
Stels SMS
Silent SMS
To manage a handset or its preinstalled applications, hackers use Type 0 Messages or so-called ‘Silent SMS’ or ‘Stealth SMS’. The key points of these type of SMS are not shown or kept on a handset. The Silent SMS request goes as well via HLR. Having HLR on our we intercept any attacks and notify our subscribers about them. The feature is included to PING.
Secure SIM has no billing at Network Operator’s side that makes it impossible to get, record and analyze any information about subscribers (CDRs, Location, Voice print etc).
Our System manages and controls all the process occurring on the three levels: Subsbcriber’s Handset (a handset with a changed system), our own identification module (Secure SIM with the imbedded applets) as well as the network level (we fully control HLR, MSC and SMSC).
PS
It is important to remember that a regular handset is highly insecure. Operators are constantly improving their tools to collect and analyze information about Subscribers using billing patterns. Having access to all national Network Operators Billing Systems, it is possible to find out a lot about a Subscriber.